LAN Technologies
ETHERNET
Ethernet was developed by DIX (Digital, Intel and Xerox) in the 1970s. In 1980 the IEEE 802.3 standard was released. Two years later version 2 was introduced, which is the basis for today’s Ethernet networks. The access method (how the wire is accessed) is Carrier Sense Multiple Access/Collision Detection (CSMA/CD). In a CSMA/CD network stations listen to check if the network is busy, if the network is free the station transmits data. When two stations listen, and both determine the network is available, they will start sending the data simultaneously and a collision occurs. When the collision is detected both stations will retransmit the data after a random wait time created by a backoff algorithm. In today’s large-fast-growing-bandwidth-eating network environments this will soon become a problem, stations will have to wait more often before they can transmit data and more collisions will occur. The solution to this is to separate the network in multiple collisions domains, which devices can be used for this purpose will be explained using a network diagram for each of the following relevant network components.
An Ethernet network is a broadcast system, this means that when a station transmits data every other station receives the data. The frames contain an address in the frame header, only the station with that address will pick up the frame and pass it on to upper-layer protocols to be processed.
BROADCAST DOMAIN
All devices in this domain will receive broadcast frames originating from any other device within the domain. Broadcast domains are typically bounded by routers because routers do not forward broadcast frames. Broadcast frames are frames explicitly directed to all nodes on the LAN, as networks grow this will become a problem as well.
REPEATERS
A repeaters is a simple device that is used to expand LANs over larger distances by connecting segments. They do not control broadcast or collision domains, they are not aware of upper-layer protocols and frame formats, they merely regenerate/amplify the signal. Repeaters operate at the Physical layer of the OSI model. An important rule when using repeaters to expand a network is the 5-4-3 rule, which defines that the maximum distance between two hosts on the same network can be 5 segments, 4 repeaters, and only 3 of the segments can be populated, as illustrated in the following logical network diagram: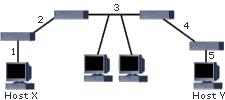 HUBS/CONCENTRATORS
HUBS/CONCENTRATORS
Hubs, also known as concentrators or multiport repeaters, are used in star/hierarchical networks to connect multiple stations/cable segments. There are two main types of hubs: passive and active. An active hub takes the incoming frames, amplifies the signal, and forwards it to all other ports, a passive hub simply splits the signal and forwards it. Another type of hubs can be managed allowing individual port configuration and traffic monitoring, these are know as intelligent- or managed hubs.
Hubs operate on the physical layer of the OSI model and they are protocol transparent, that means they are not aware of the upper-layer protocols and such as IP, IPX nor MAC addressing. Hence they do not control broadcast or collision domains, but they extend them as illustrated below:
BRIDGES
Bridges are more intelligent than hubs; they operate on the Data Link layer of the OSI model.
They are used to increase network performance by segmenting networks in separate collision domains. Bridges are also protocol transparent, they are not aware of the upper-layer protocols. They keep a table with MAC addresses of all nodes, and on which segment they are located.
A bridge takes an incoming frame, reads its destination MAC address and consults the database to decide what should be done with the frame; if the location of the destination MAC address is listed in the database, the frame is forwarded to the corresponding port. If the destination port is the same as the port where the frame arrived it will be discarded. If the location is not known the frame will be flooded through all outgoing ports/segments.
As illustrated below, bridges control collision domains, they do not control broadcast domains: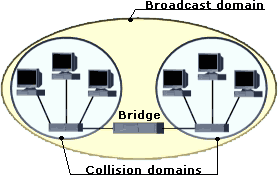
SWITCHES
To improve network performance even more switches were developed, switches are very similar to bridges; they also keep a table with MAC addresses per port to make switching decisions, operate in the OSI model and are protocol transparent.
Some of the main differences are:
- a switch has more ports than a bridge
- bridges switch in software whereas switches switch in hardware (integrated circuits)
- switches offer more variance in speed, an individual port can be assigned 10 Mb/s or 100 Mb/s or even more.
As illustrated below, switches control collision domains, they do not control broadcast domains*: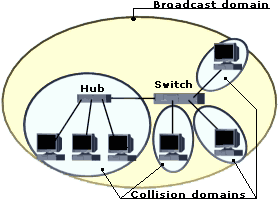
* Do not control broadcast domains unless Virtual Local Area Networks (VLANs) are being used, and most modern switches do support VLANs. The following diagram represents a router configured with two VLANs. Like in the previous diagram each port forms an collision domain, but as you can see in this diagram the network is separated in two broadcast domains using VLANs. If the network protocol used in this network would be TCP/IP the VLANs would each have its own (sub-)network address, for example VLAN 1 could be Class C 192.168.110.x and VLAN 2 192.168.220.x.
Switches are able to use software to create Virtual LANs; a logical grouping of network devices where the members can be on different physical segments. A VLAN can be based on Port IDs, MAC addresses, protocols or applications. For example in the network diagram above port 1 to 12 on the switch could be assigned to VLAN 1, and port 13 to 24 to VLAN 2, resulting in two different broadcast domains, or station 1, 2 and 3 could be using IPX/SPX while station 4, 5 and 6 could be using TCP/IP.
An example of a large network with VLANs could be an office building with a switch on each of the three floors and a main switch connecting them all together. An administrator would be able to keep a list of MAC addresses and assign stations from different floors to a single VLAN and for example create a VLAN (broadcast domain) for each department in the company. Switches share their MAC address table information with other switches so the path to a destination can be found quickly.
ROUTERS
Routers are used to interconnect multiple (sub-)networks and route information between these networks by choosing an optimal path (“route”) to the destination. They operate on the Network layer (Layer 3) of the OSI model and in contradiction to hubs, bridges and switches, routers are protocol-aware. Examples of these protocols are: IP, IPX, and AppleTalk. Routers make forwarding decisions based on a table with network addresses and there corresponding ports, this table is known as the route table. Common use of routers is to connect two different type of networks (for example Ethernet and Token ring) or to interconnect LANs into a WAN. The concept of routing will be covered in more detail in the Routing Protocols TechNote.
As illustrated below, routers control collision domains AND broadcast domains:
GATEWAYS
A gateway (as a network component) is a device that connects networks with dissimilar network protocols or architectures and translates between the networks. Gateways are very intelligent devices, generally they operate on the Transport layer and on those above it (Session, Presentation, Application). A gateway could be used to allow IPX/SPX clients to use a gateway with a TCP/IP uplink to an internet connection. TCP/IP would be converted to IPX/SPX. Another common use of a gateway is to connect an Ethernet network to an IBM SNA mainframe environment.
NICs
A NIC (Network Interface Card) is an expansion cards for a computer used to connect a to the physical network. The NIC’s interface itself is defined at the Physical layer (Layer 1) of the OSI model, the physical address (also known as Burned-In Address and commonly: MAC address) of the adapter as well as the drivers to control the NIC are located at the Data Link layer’s MAC sub-layer. The reason the physical address is defined at the Data Link layer is that the Physical layer only handles bits.
Half duplex
Half-duplex means that only one host can communicate at a given time, two hosts communicating with each other will take turns transmitting. This is the default on non-switched LANs.
Full-duplex
In full-duplex communication both hosts can transmit at the same time, theoretical allowing twice as much data to be transmitted over the same connection.
In order for full-duplex to work, some requirements must be met:
- The NICs, hubs etc. must support it,
- Collision Detection and Loopback functions must be disabled.
In reality the connections able to run at full-duplex are cross-cable connections and connection to a port on a switch, where collisions cannot occur because each end has it’s own wire pair (segment).